 |
| October 25, 2016 | Volume 12 Issue 40 |
Electrical/Electronic News & Products
Designfax weekly eMagazine
Archives
Partners
Manufacturing Center
Product Spotlight
Modern Applications News
Metalworking Ideas For
Today's Job Shops
Tooling and Production
Strategies for large
metalworking plants
Intro to reed switches, magnets, magnetic fields
 This brief introductory video on the DigiKey site offers tips for engineers designing with reed switches. Dr. Stephen Day, Ph.D. from Coto Technology gives a solid overview on reed switches -- complete with real-world application examples -- and a detailed explanation of how they react to magnetic fields.
This brief introductory video on the DigiKey site offers tips for engineers designing with reed switches. Dr. Stephen Day, Ph.D. from Coto Technology gives a solid overview on reed switches -- complete with real-world application examples -- and a detailed explanation of how they react to magnetic fields.
View the video.
Bi-color LEDs to light up your designs
 Created with engineers and OEMs in mind, SpectraBright Series SMD RGB and Bi-Color LEDs from Visual Communi-cations Company (VCC) deliver efficiency, design flexibility, and control for devices in a range of industries, including mil-aero, automated guided vehicles, EV charging stations, industrial, telecom, IoT/smart home, and medical. These 50,000-hr bi-color and RGB options save money and space on the HMI, communicating two or three operating modes in a single component.
Created with engineers and OEMs in mind, SpectraBright Series SMD RGB and Bi-Color LEDs from Visual Communi-cations Company (VCC) deliver efficiency, design flexibility, and control for devices in a range of industries, including mil-aero, automated guided vehicles, EV charging stations, industrial, telecom, IoT/smart home, and medical. These 50,000-hr bi-color and RGB options save money and space on the HMI, communicating two or three operating modes in a single component.
Learn more.
All about slip rings: How they work and their uses
 Rotary Systems has put together a really nice basic primer on slip rings -- electrical collectors that carry a current from a stationary wire into a rotating device. Common uses are for power, proximity switches, strain gauges, video, and Ethernet signal transmission. This introduction also covers how to specify, assembly types, and interface requirements. Rotary Systems also manufactures rotary unions for fluid applications.
Rotary Systems has put together a really nice basic primer on slip rings -- electrical collectors that carry a current from a stationary wire into a rotating device. Common uses are for power, proximity switches, strain gauges, video, and Ethernet signal transmission. This introduction also covers how to specify, assembly types, and interface requirements. Rotary Systems also manufactures rotary unions for fluid applications.
Read the overview.
Seifert thermoelectric coolers from AutomationDirect
 Automation-Direct has added new high-quality and efficient stainless steel Seifert 340 BTU/H thermoelectric coolers with 120-V and 230-V power options. Thermoelectric coolers from Seifert use the Peltier Effect to create a temperature difference between the internal and ambient heat sinks, making internal air cooler while dissipating heat into the external environment. Fans assist the convective heat transfer from the heat sinks, which are optimized for maximum flow.
Automation-Direct has added new high-quality and efficient stainless steel Seifert 340 BTU/H thermoelectric coolers with 120-V and 230-V power options. Thermoelectric coolers from Seifert use the Peltier Effect to create a temperature difference between the internal and ambient heat sinks, making internal air cooler while dissipating heat into the external environment. Fans assist the convective heat transfer from the heat sinks, which are optimized for maximum flow.
Learn more.
EMI shielding honeycomb air vent panel design
 Learn from the engineering experts at Parker how honeycomb air vent panels are used to help cool electronics with airflow while maintaining electromagnetic interference (EMI) shielding. Topics include: design features, cell size and thickness, platings and coatings, and a stacked design called OMNI CELL construction. These vents can be incorporated into enclosures where EMI radiation and susceptibility is a concern or where heat dissipation is necessary. Lots of good info.
Learn from the engineering experts at Parker how honeycomb air vent panels are used to help cool electronics with airflow while maintaining electromagnetic interference (EMI) shielding. Topics include: design features, cell size and thickness, platings and coatings, and a stacked design called OMNI CELL construction. These vents can be incorporated into enclosures where EMI radiation and susceptibility is a concern or where heat dissipation is necessary. Lots of good info.
Read the Parker blog.
What is 3D-MID? Molded parts with integrated electronics from HARTING
 3D-MID (three-dimensional mechatronic integrated devices) technology combines electronic and mechanical functionalities into a single, 3D component. It replaces the traditional printed circuit board and opens up many new opportunities. It takes injection-molded parts and uses laser-direct structuring to etch areas of conductor structures, which are filled with a copper plating process to create very precise electronic circuits. HARTING, the technology's developer, says it's "Like a PCB, but 3D." Tons of possibilities.
3D-MID (three-dimensional mechatronic integrated devices) technology combines electronic and mechanical functionalities into a single, 3D component. It replaces the traditional printed circuit board and opens up many new opportunities. It takes injection-molded parts and uses laser-direct structuring to etch areas of conductor structures, which are filled with a copper plating process to create very precise electronic circuits. HARTING, the technology's developer, says it's "Like a PCB, but 3D." Tons of possibilities.
View the video.
Loss-free conversion of 3D/CAD data
 CT CoreTech-nologie has further developed its state-of-the-art CAD converter 3D_Evolution and is now introducing native interfaces for reading Solidedge and writing Nx and Solidworks files. It supports a wide range of formats such as Catia, Nx, Creo, Solidworks, Solidedge, Inventor, Step, and Jt, facilitating smooth interoperability between different systems and collaboration for engineers and designers in development environments with different CAD systems.
CT CoreTech-nologie has further developed its state-of-the-art CAD converter 3D_Evolution and is now introducing native interfaces for reading Solidedge and writing Nx and Solidworks files. It supports a wide range of formats such as Catia, Nx, Creo, Solidworks, Solidedge, Inventor, Step, and Jt, facilitating smooth interoperability between different systems and collaboration for engineers and designers in development environments with different CAD systems.
Learn more.
Top 5 reasons for solder joint failure
 Solder joint reliability is often a pain point in the design of an electronic system. According to Tyler Ferris at ANSYS, a wide variety of factors affect joint reliability, and any one of them can drastically reduce joint lifetime. Properly identifying and mitigating potential causes during the design and manufacturing process can prevent costly and difficult-to-solve problems later in a product lifecycle.
Solder joint reliability is often a pain point in the design of an electronic system. According to Tyler Ferris at ANSYS, a wide variety of factors affect joint reliability, and any one of them can drastically reduce joint lifetime. Properly identifying and mitigating potential causes during the design and manufacturing process can prevent costly and difficult-to-solve problems later in a product lifecycle.
Read this informative ANSYS blog.
Advanced overtemp detection for EV battery packs
 Littelfuse has introduced TTape, a ground-breaking over-temperature detection platform designed to transform the management of Li-ion battery systems. TTape helps vehicle systems monitor and manage premature cell aging effectively while reducing the risks associated with thermal runaway incidents. This solution is ideally suited for a wide range of applications, including automotive EV/HEVs, commercial vehicles, and energy storage systems.
Littelfuse has introduced TTape, a ground-breaking over-temperature detection platform designed to transform the management of Li-ion battery systems. TTape helps vehicle systems monitor and manage premature cell aging effectively while reducing the risks associated with thermal runaway incidents. This solution is ideally suited for a wide range of applications, including automotive EV/HEVs, commercial vehicles, and energy storage systems.
Learn more.
Benchtop ionizer for hands-free static elimination
 EXAIR's Varistat Benchtop Ionizer is the latest solution for neutralizing static on charged surfaces in industrial settings. Using ionizing technology, the Varistat provides a hands-free solution that requires no compressed air. Easily mounted on benchtops or machines, it is manually adjustable and perfect for processes needing comprehensive coverage such as part assembly, web cleaning, printing, and more.
EXAIR's Varistat Benchtop Ionizer is the latest solution for neutralizing static on charged surfaces in industrial settings. Using ionizing technology, the Varistat provides a hands-free solution that requires no compressed air. Easily mounted on benchtops or machines, it is manually adjustable and perfect for processes needing comprehensive coverage such as part assembly, web cleaning, printing, and more.
Learn more.
LED light bars from AutomationDirect
 Automation-Direct adds CCEA TRACK-ALPHA-PRO series LED light bars to expand their offering of industrial LED fixtures. Their rugged industrial-grade anodized aluminum construction makes TRACKALPHA-PRO ideal for use with medium to large-size industrial machine tools and for use in wet environments. These 120 VAC-rated, high-power LED lights provide intense, uniform lighting, with up to a 4,600-lumen output (100 lumens per watt). They come with a standard bracket mount that allows for angle adjustments. Optional TACLIP mounts (sold separately) provide for extra sturdy, vibration-resistant installations.
Automation-Direct adds CCEA TRACK-ALPHA-PRO series LED light bars to expand their offering of industrial LED fixtures. Their rugged industrial-grade anodized aluminum construction makes TRACKALPHA-PRO ideal for use with medium to large-size industrial machine tools and for use in wet environments. These 120 VAC-rated, high-power LED lights provide intense, uniform lighting, with up to a 4,600-lumen output (100 lumens per watt). They come with a standard bracket mount that allows for angle adjustments. Optional TACLIP mounts (sold separately) provide for extra sturdy, vibration-resistant installations.
Learn more.
World's first metalens fisheye camera
 2Pi Optics has begun commercial-ization of the first fisheye camera based on the company's proprietary metalens technology -- a breakthrough for electronics design engineers and product managers striving to miniaturize the tiny digital cameras used in advanced driver-assistance systems (ADAS), AR/VR, UAVs, robotics, and other industrial applications. This camera can operate at different wavelengths -- from visible, to near IR, to longer IR -- and is claimed to "outperform conventional refractive, wide-FOV optics in all areas: size, weight, performance, and cost."
2Pi Optics has begun commercial-ization of the first fisheye camera based on the company's proprietary metalens technology -- a breakthrough for electronics design engineers and product managers striving to miniaturize the tiny digital cameras used in advanced driver-assistance systems (ADAS), AR/VR, UAVs, robotics, and other industrial applications. This camera can operate at different wavelengths -- from visible, to near IR, to longer IR -- and is claimed to "outperform conventional refractive, wide-FOV optics in all areas: size, weight, performance, and cost."
Learn more.
Orbex offers two fiber optic rotary joint solutions
 Orbex Group announces its 700 Series of fiber optic rotary joint (FORJ) assemblies, supporting either single or multi-mode operation ideal for high-speed digital transmission over long distances. Wavelengths available are 1,310 or 1,550 nm. Applications include marine cable reels, wind turbines, robotics, and high-def video transmission. Both options feature an outer diameter of 7 mm for installation in tight spaces. Construction includes a stainless steel housing.
Orbex Group announces its 700 Series of fiber optic rotary joint (FORJ) assemblies, supporting either single or multi-mode operation ideal for high-speed digital transmission over long distances. Wavelengths available are 1,310 or 1,550 nm. Applications include marine cable reels, wind turbines, robotics, and high-def video transmission. Both options feature an outer diameter of 7 mm for installation in tight spaces. Construction includes a stainless steel housing.
Learn more.
Mini tunnel magneto-resistance effect sensors
 Littelfuse has released its highly anticipated 54100 and 54140 mini Tunnel Magneto-Resistance (TMR) effect sensors, offering unmatched sensitivity and power efficiency. The key differentiator is their remarkable sensitivity and 100x improvement in power efficiency compared to Hall Effect sensors. They are well suited for applications in position and limit sensing, RPM measurement, brushless DC motor commutation, and more in various markets including appliances, home and building automation, and the industrial sectors.
Littelfuse has released its highly anticipated 54100 and 54140 mini Tunnel Magneto-Resistance (TMR) effect sensors, offering unmatched sensitivity and power efficiency. The key differentiator is their remarkable sensitivity and 100x improvement in power efficiency compared to Hall Effect sensors. They are well suited for applications in position and limit sensing, RPM measurement, brushless DC motor commutation, and more in various markets including appliances, home and building automation, and the industrial sectors.
Learn more.
Panasonic solar and EV components available from Newark
 Newark has added Panasonic Industry's solar inverters and EV charging system components to their power portfolio. These best-in-class products help designers meet the growing global demand for sustainable and renewable energy mobility systems. Offerings include film capacitors, power inductors, anti-surge thick film chip resistors, graphite thermal interface materials, power relays, capacitors, and wireless modules.
Newark has added Panasonic Industry's solar inverters and EV charging system components to their power portfolio. These best-in-class products help designers meet the growing global demand for sustainable and renewable energy mobility systems. Offerings include film capacitors, power inductors, anti-surge thick film chip resistors, graphite thermal interface materials, power relays, capacitors, and wireless modules.
Learn more.
Georgia Tech study finds 'lurking malice' in cloud hosting services
By John Toon
A study of 20 major cloud hosting services has found that as many as 10 percent of the repositories hosted by them had been compromised -- with several hundred of the "buckets" actively providing malware. Such bad content could be challenging to find, however, because it can be rapidly assembled from stored components that individually may not appear to be malicious.
To identify the bad content, researchers created a scanning tool that looks for features unique to the bad repositories, known as "Bars." The features included certain types of redirection schemes and "gatekeeper" elements designed to protect the malware from scanners. Researchers from the Georgia Institute of Technology, Indiana University Bloomington, and the University of California Santa Barbara conducted the study.
Believed to be the first systematic study of cloud-based malicious activity, the research was presented October 24 at the ACM Conference on Computer and Communications Security in Vienna, Austria. The work was supported in part by the National Science Foundation.
"Bad actors have migrated to the cloud along with everybody else," said Raheem Beyah, a professor in Georgia Tech's School of Electrical and Computer Engineering. "The bad guys are using the cloud to deliver malware and other nefarious things while remaining undetected. The resources they use are compromised in a variety of ways, from traditional exploits to simply taking advantage of poor configurations."
Beyah and graduate student Xiaojing Liao found that the bad actors could hide their activities by keeping components of their malware in separate repositories that by themselves didn't trigger traditional scanners. Only when they were needed to launch an attack were the different parts of this malware assembled.
"Some exploits appear to be benign until they are assembled in a certain way," explained Beyah, who is the Motorola Foundation Professor and associate chair for strategic initiatives and innovation in the School of Electrical and Computer Engineering. "When you scan the components in a piecemeal kind of way, you only see part of the malware, and the part you see may not be malicious."
In the cloud, malicious actors take advantage of how difficult it can be to scan so much storage. Operators of cloud hosting services may not have the resources to do the deep scans that may be necessary to find the Bars -- and their monitoring of repositories may be limited by service-level agreements.
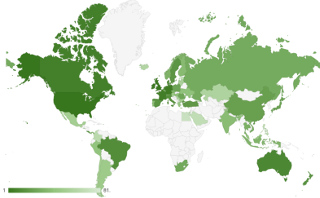
This map shows locations where the impacts of bad repositories (Bars) occur. [Credit: Xiaojing Liao, Georgia Tech]
While splitting the malicious software up helped hide it, the strategy also created a technique for finding the "bad buckets" hosting it, Beyah said. Many of the bad actors had redundant repositories connected by specific kinds of redirection schemes that allowed attacks to continue if one bucket were lost. The bad buckets also usually had "gatekeepers" designed to keep scanners out of the repositories, and where webpages were served, they had simple structures that were easy to propagate.
"We observed that there is an inherent structure associated with how these attackers have set things up," he explained. "For instance, the bad guys all had bodyguards at the door. That's not normal for cloud storage, and we used that structure to detect them."
The researchers began by studying a small number of known bad repositories to understand how they were being used. Based on what they learned, they created "BarFinder," a scanner tool that automatically searches for and detects features common to the bad repositories.
Overall, the researchers scanned more than 140,000 sites on 20 cloud hosting sites and found about 700 active repositories for malicious content. In total, about 10 percent of cloud repositories the team studied had been compromised in some way. The researchers notified the cloud hosting companies of their findings before publication of the study.
"It's pervasive in the cloud," said Beyah. "We found problems in every last one of the hosting services we studied. We believe this is a significant problem for the cloud hosting industry."
In some cases, the bad actors simply opened an inexpensive account and began hosting their software. In other cases, the malicious content was hidden in the cloud-based domains of well-known brands. Intermingling the bad content with good content in the brand domains protected the malware from blacklisting of the domain.
Beyah and Liao saw a wide range of attacks in the cloud-hosted repositories, ranging from phishing and common drive-by downloads to fake antivirus and computer update sites. "They can attack you directly from these buckets, or they can redirect you to other malicious buckets or a series of malicious buckets," he said. "It can be difficult to see where the code is redirecting you."
To protect cloud-based repositories from these attacks, Beyah recommends the usual defenses, including patching of systems and proper configuration settings.
Looking ahead, the researchers hope to make BarFinder available to a broader audience. That could include licensing the technology to a security company, or making it available as an open-source tool.
"Attackers are very clever, and as we secure things and make the cloud infrastructure more challenging for them to attack, they will move onto something else," he said. "In the meantime, every system that we can secure makes the internet just a little bit safer."
Source: Georgia Tech
Published October 2016
Rate this article
View our terms of use and privacy policy
